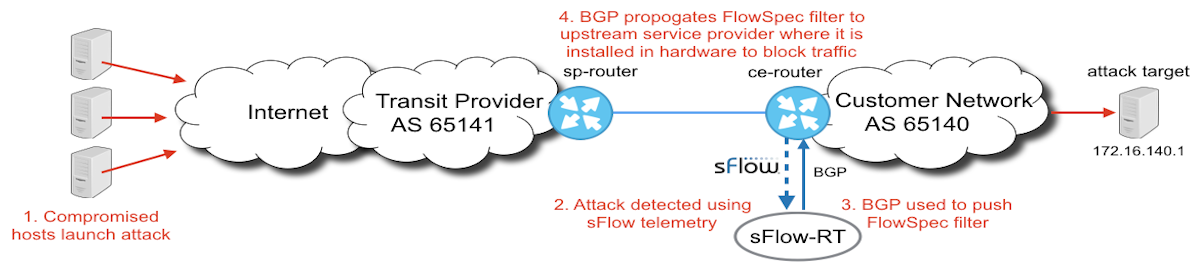
DDoS Mitigation with sFlow-rt & Flowspec
If you ever wanted to setup a simple and FREE system to mitigate ddos/dos attacks, then sFlow-rt is the way to go. It’s simple to setup and configure.
You can find installation instructions here: https://sflow-rt.com/intro.php
Once you install it, you can find the ddos-protect module along with installation instructions here: https://github.com/sflow-rt/ddos-protect
Once all that is done, you can start modifying it for your environment. In our clients case, there were 2 edge routers that we had to create the bgp sessions to where we wanted the flowspec rules pushed to.
The edge routers in this case were Juniper MX240’s. The config for the sessions looked like so:
set protocols bgp group IBGP-DDOS neighbor x.x.x.x local-address y.y.y.y
set protocols bgp group IBGP-DDOS neighbor x.x.x.x family inet unicast prefix-limit maximum 100
set protocols bgp group IBGP-DDOS neighbor x.x.x.x family inet unicast prefix-limit teardown
set protocols bgp group IBGP-DDOS neighbor x.x.x.x family inet flow no-validate DDOS_FS_POLICY #Enables flowspec
set protocols bgp group IBGP-DDOS neighbor x.x.x.x export IBGP-DDOS-EXPORT #Prevents the routers from sending routes TO the flowspec server
set protocols bgp group IBGP-DDOS neighbor x.x.x.x peer-as 22418
set policy-options policy-statement DDOS_FS_POLICY from neighbor x.x.x.x
set policy-options policy-statement DDOS_FS_POLICY then accept
set policy-options policy-statement IBGP-DDOS-EXPORT term DENY_ALL then reject
Some notes for the install/setup for issues we encontered.
In start.sh, change the memory to 4G or higher:
RTMEM="${RTMEM:-4G}"
Create a ddos config file with all options you want. Modify the values below as needed to fit your setup.
bgp.port=179
bgp.start=yes
ddos_protect.router=x.x.x.x,y.y.y.y
ddos_protect.as=xxxxx
ddos_protect.id=0.6.6.6
ddos_protect.nexthop=null0
ddos_protect.localpref=666
ddos_protect.enable.ipv6=no
ddos_protect.enable.flowspec=yes
ddos_protect.flowspec.rate=12500
ddos_protect.flowspec.redirect.method=as
ddos_protect.flowspec.redirect.as=xxxxx:666
ddos_protect.flowspec.redirect.as4=xxxxx:666
ddos_protect.flowspec.community=128:6:0
ddos_protect.maxroutes=1000
ddos_protect.maxflows=100
ddos_protect.externalgroup=external
ddos_protect.excludedgroups=exclude
ddos_protect.ip_flood.action=filter
ddos_protect.ip_flood.threshold=500000
ddos_protect.ip_flood.timeout=180
ddos_protect.ip_fragmentation.action=filter
ddos_protect.ip_fragmentation.threshold=50000
ddos_protect.ip_fragmentation.timeout=60
ddos_protect.icmp_flood.action=filter
ddos_protect.icmp_flood.threshold=50000
ddos_protect.icmp_flood.timeout=60
ddos_protect.tcp_amplification.action=ignore
ddos_protect.tcp_amplification.threshold=50000
ddos_protect.tcp_amplification.timeout=60
ddos_protect.tcp_flood.action=filter
ddos_protect.tcp_flood.threshold=1000000
ddos_protect.tcp_flood.timeout=60
ddos_protect.udp_flood.action=filter
ddos_protect.udp_flood.threshold=500000
ddos_protect.udp_flood.timeout=60
ddos_protect.udp_amplification.action=filter
ddos_protect.udp_amplification.threshold=50000
ddos_protect.udp_amplification.timeout=60
ddos_protect.mode=automatic
ddos_protect.flow_seconds=2
ddos_protect.threshold_seconds=60
ddos_protect.esr=no
ddos_protect.esr_samples=15
ddos_protect.syslog.host=Comma
ddos_protect.syslog.port=514
ddos_protect.syslog.facility=16
ddos_protect.syslog.severity=5
Once that is done, create a simple script that you can run at will or on startup to start sflow-rt based on the config file above:
#!/bin/sh
./sflow-rt/start.sh -Dsystem.propertyFiles=/root/ddos.conf &Once it’s running, you can access the gui at http://x.x.x.x:8008/app/ddos-protect/html/index.html. You can then also change your settings from the Settings tab as needed. You’ll need to tune the tcp/udp/icmp values for your environment so you don’t start dropping legitimate traffic.